More actions
| Line 3: | Line 3: | ||
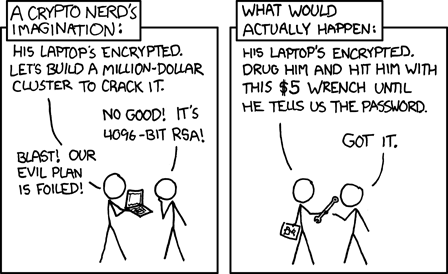
== $5 Wrench Attack == | == $5 Wrench Attack == | ||
A $5 Wrench Attack is a physical or social engineering [[attack]] where an attacker uses coercion, intimidation, or violence—symbolized by a cheap tool like a $5 | A $5 Wrench Attack is a physical or social engineering [[attack]] where an attacker uses coercion, intimidation, or violence—symbolized by a cheap tool like a [[$5 wrench]]—to force a [[Bitcoin]] user to reveal their private keys, [[Seed Phrase|seed phrase]], or access to their [[crypto]] funds. Unlike digital cyberattacks (e.g., [[hacking]] or [[phishing]]), this attack targets the human element, exploiting physical or psychological vulnerabilities. | ||
TLDR | TLDR | ||
Revision as of 04:35, 8 May 2025
inspired by An Unending Variety of Topics by Nick Szabo https://unenumerated.blogspot.com/
$5 Wrench Attack
A $5 Wrench Attack is a physical or social engineering attack where an attacker uses coercion, intimidation, or violence—symbolized by a cheap tool like a $5 wrench—to force a Bitcoin user to reveal their private keys, seed phrase, or access to their crypto funds. Unlike digital cyberattacks (e.g., hacking or phishing), this attack targets the human element, exploiting physical or psychological vulnerabilities.
TLDR
Bad guys will kidnap and torture you for your bitcoin.
Prevention Strategies:
- Maintain OPSEC Avoid publicly disclosing Bitcoin holdings or wealth. Use pseudonyms online and limit sharing on social media.
- Don't buy a Lambo. Win one!
- Store seed phrases and hardware wallets in secure locations, such as a safe deposit box or a hidden safe. Consider tamper-evident storage solutions. Remember that safes are not safe!
- Use multi-signature (multisig) setups requiring multiple keys held in different locations or by trusted parties, making coercion less effective.
- Geographic Distribution: Store backups (e.g., seed phrase copies) in multiple secure locations to reduce the risk of losing everything in one attack. Consider storing keys in different government jurisdications to avoid a 6102 attack.
- Duress Codes: Some hardware wallets support duress PINs that unlock a decoy wallet with minimal funds, misleading attackers.
- Wrench Defense: Set up a Bitcoin tripwire in a decoy wallet on your phone. Trigger the silent alarm during a wrench attack to share your location with law enforcement or Liam Neeson.
Wrench Defense
MediaWiki has been installed.
Consult the User's Guide for information on using the wiki software.
Getting started
- Configuration settings list
- MediaWiki FAQ
- MediaWiki release mailing list
- Localise MediaWiki for your language
- Learn how to combat spam on your wiki
Books
Essential Reading
The Bitcoin Standard
Layered Money
The Price of Tomorrow
The Book of Satoshi
Broken Money
Inventing Bitcoin
Mastering Bitcoin
Everything Divided by 21 Million
The Sovereign Individual
The Creature from Jekyll Island
Products
spot for affiliate plugs