More actions
| Line 48: | Line 48: | ||
=== Cultural Significance === | === Cultural Significance === | ||
The $5 wrench attack serves as a reminder of the trade-offs between self-sovereignty and security. It reinforces the philosophy of "not your keys, not your coins," while highlighting that true financial freedom requires robust personal responsibility and vigilance in both digital and physical realms. | |||
== Prevention Strategies: == | == Prevention Strategies: == | ||
Revision as of 10:03, 10 May 2025
inspired by An Unending Variety of Topics by Nick Szabo https://unenumerated.blogspot.com/
Bitcoin Essentials
- Bitcoin Only
- What's the first rule of Bitcoin? OPSEC
- Master list of hardware/tech
- Master list of seed backups
- Master list of Bitcoin books
- Fun Facts
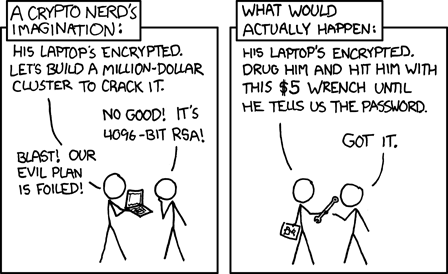
$5 Wrench Attack
A wrench attack is a colloquial term used to describe a physical coercion method aimed at extracting private keys or other sensitive information from a cryptocurrency holder. The term emphasizes the vulnerability of even the most secure digital systems to low-tech, real-world threats, such as physical violence or intimidation, using a cheap tool like a $5 wrench as a metaphor. No amount of digital encryption can prevent an attacker from using force to compel a victim to reveal their private keys or seed phrases.
TLDR
Bad guys will kidnap and torture you for your bitcoin.
A $5 wrench attack typically involves:
- Targeting: An attacker identifies a Bitcoin holder, often through public displays of wealth, social media posts, or compromised personal information.
- Coercion: The attacker uses threats, physical violence, or intimidation (symbolized by the "$5 wrench") to force the victim to disclose their private keys, seed phrases, or access to their wallet.
- Access: With the obtained information, the attacker transfers the victim's bitcoin to their own wallet, often irreversibly due to the decentralized and pseudonymous nature of the blockchain.
Protecting private keys requires not only digital safeguards like hardware wallets and multi-signature setups, but also physical and personal security measures like Wrench Defense. Unlike traditional banking systems, Bitcoin offers no centralized authority to reverse fraudulent transactions, making prevention absolutely critical.
Mitigation Strategies
To reduce the risk of a wrench attack:
- Use multi-signature wallets, requiring multiple keys held in different locations or by trusted parties.
- Store seed phrases in secure, tamper-evident locations, such as safety deposit boxes or encrypted physical backups.
- Consider geographic diversification of key storage to reduce the likelihood of simultaneous physical access.
- Practice discretion by avoiding public discussions of Bitcoin holdings.
- Employ decoy wallets with small amounts of bitcoin to satisfy attackers without revealing primary funds.
- Set up a tripwire in a decoy wallet that automatically sends out an SOS if you're wrench attacked.
Cultural Significance
The $5 wrench attack serves as a reminder of the trade-offs between self-sovereignty and security. It reinforces the philosophy of "not your keys, not your coins," while highlighting that true financial freedom requires robust personal responsibility and vigilance in both digital and physical realms.
Prevention Strategies:
- Maintain OPSEC. Avoid publicly disclosing Bitcoin holdings or wealth. Use pseudonyms online and limit sharing on social media. Follow @WrenchDefense if you're a Bitcoin psychopath, we follow all toxic plebs!
- Don't buy a Lambo. Win one instead!
- Minimize your digital footprint. Use TOR or a VPN. Run TailsOS on a Linux distro like Ubuntu. Avoid all KYC exchanges and services.
- Use a dedicated computer for Bitcoin activities. If it's a laptop, remove the Wi-fi card.
- Store seed phrases and hardware wallets in secure locations, such as a safe deposit box or a hidden safe. Consider tamper-evident storage solutions. Remember that safes are not safe!
- Use multi-signature (multisig) wallets requiring multiple keys held in different locations or by trusted parties, making coercion less effective.
- Geographic Distribution: Store metal backups (e.g., seed phrase copies) in multiple secure locations to reduce the risk of losing everything in one attack. Consider storing keys in different government jurisdications to avoid a 6102 attack.
- Get a gun, consider self-defense training, and install a home security system.
- Duress Codes: Some hardware wallets support duress PINs that unlock a decoy wallet with minimal funds, misleading attackers.
- Wrench Defense: Set up a Bitcoin tripwire in a decoy wallet on your phone. Trigger the silent alarm during a wrench attack to share your location with law enforcement or Liam Neeson.
Wrench Defense
MediaWiki has been installed.
Consult the User's Guide for information on using the wiki software.